When you're traveling abroad, your phone is your lifeline—and also your biggest liability.
Cellular networks were built for interoperability, not privacy. As your phone hops between countries, it connects to local telecom providers so you can keep calling, texting, and using data. But not all networks are secure, and not all governments treat privacy the same. Many have been infiltrated by hackers. And almost all participate in a system that was never designed to protect you.
Cape was built to change that. Our secure global coverage gives you the power of international roaming without exposing your identity or communications. Here’s how we do it—and what we protect you from.
The Risks of Standard Global Roaming
Insider Access at Telecom Networks
It’s widely acknowledged that nation states and hackers have successfully gained access to telecom networks—both large and small—around the world. This isn’t just about remote hacks; it’s about insiders. From state-sponsored attacks like Volt Typhoon and Salt Typhoon to routine abuses of lawful intercept systems, telecom infrastructure has become a powerful surveillance tool. Many networks are owned or operated by foreign governments, giving them direct access to subscriber data. Others have been compromised through social engineering, bribery, or exploitation of third-parties with privileged access.
Once inside, attackers can access a wide range of sensitive information: personal details, message contents, websites visited, real-time and historical location, and records of who you communicate with. In legacy networks, this data exposure is the norm. And when you roam through these networks, your information is at risk.
Close Technical Surveillance (CTS)
When you land at an airport, check in at an embassy, or walk past a foreign HQ, your phone is vulnerable to Close Technical Surveillance (CTS). These attacks use false base stations (a.k.a. cell site simulators or “IMSI catchers”) to capture your identifiers. From there, adversaries can track your movements or deanonymize your SIM.
For example: A malicious actor could use a cell site simulator to grab your subscriber ID, or IMSI, as soon as you land. If you're roaming through a major carrier, they can query your home operator using their insider access to identify who you are and where you’re from.
Compromised Local SIMs
Using a local SIM while traveling is convenient, but risky. The local network now owns all authentication and routing, and has full access to your information, including the contents of your calls and texts, and URLs or IP addresses of your data sessions.
While modern eSIM marketplaces (like Airalo, Holafly, Gigsky) make it easy to get a local profile, when you use them, you’re handing total control over to that provider—including operators in countries where surveillance is standard practice. Popular travel eSIMs route traffic to undisclosed networks and countries known for state sponsored telecom surveillance. Even when roaming to “friendly” nations, network operators have likely been infiltrated by bad actors who can snoop on telecom traffic and pull information about subscribers of interest.
Local Breakout Roaming
Some roaming arrangements route your traffic through the foreign carrier’s core network. This practice, called "local breakout," puts your metadata, call and text contents, and browsing data directly into the hands of the local network. And many of these networks monetize or leak this information, whether to advertisers or foreign government services.
Signaling Attacks
The global network infrastructure was designed to ensure that calls, texts, and data could travel seamlessly across different networks worldwide. Signaling protocols like SS7 and Diameter were introduced to help carriers exchange information and provide connectivity across borders. But these protocols were built for interoperability, not for security.
Because these protocols assume trust in the network, attackers can abuse them to carry out attacks like tracking location, or silently rerouting messages meant for your number; these are known as signaling attacks. Adversaries can pose as a foreign network, claiming that you’re in that country and your phone is attempting to connect to their network. Some carriers may be able to detect the feasibility of the request. For example, if you recently took off from a flight out of Nashville, but an hour later, a carrier from China is now claiming that you have shown up on your network, your home carrier may be able to deduce the unlikelihood that you arrived in China so quickly, and deny the request to connect. However, hackers are evolving, and now may strategically send network attach requests from more realistic locations, like the Bahamas, tricking your home carrier into thinking you are actually in the Bahamas, and routing your phone to their malicious network.
SIM Swaps
SIM swaps are attacks where hackers and bad actors steal your phone number—intercepting your calls, texts, and even 2FA codes to hijack your accounts. These attacks are done through social engineering—by impersonating you on a support call, or using leaked personal info to pass identity checks. In some cases, attackers even bribe or threaten carrier employees to transfer your number to a new SIM.
Lawful Intercept Abuse
Almost every country has laws that allow telecom networks to intercept calls, texts, and data for law enforcement purposes. In some countries, these systems are abused to surveil journalists, political opponents, executives, or foreign visitors of interest. Some governments even require local telcos to disable encryption altogether.
How Cape Protects You Abroad
Cape has implemented multiple layers of protections against these potential threats while you’re roaming abroad. They include:
Secure Core Network
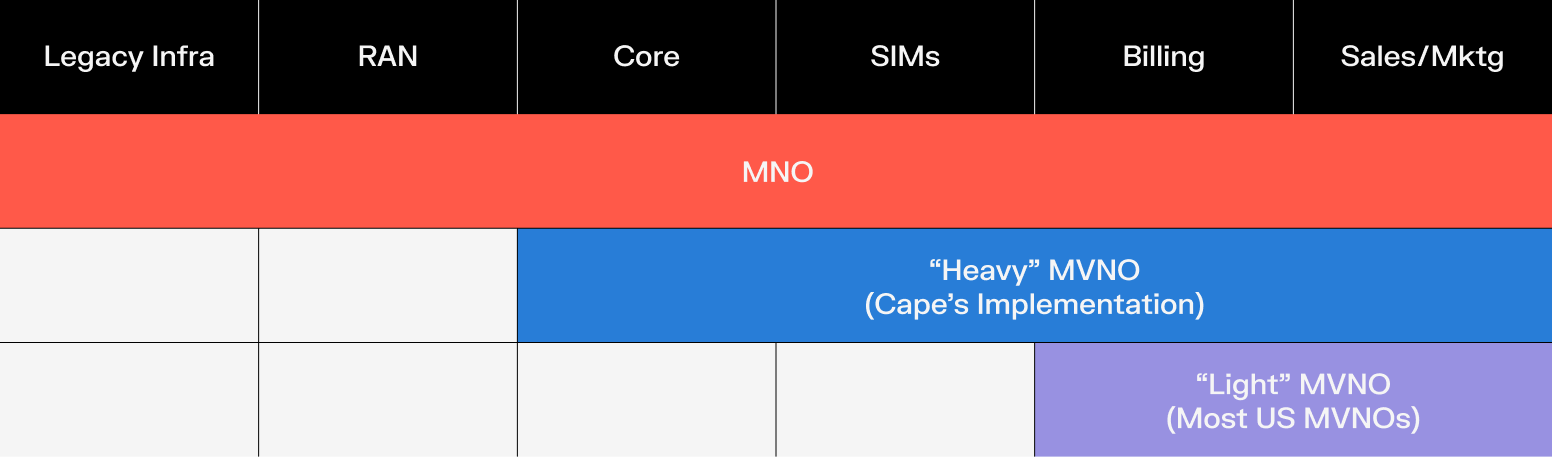
In the world of Mobile Virtual Network Operators (MVNO), there is a range of infrastructure that the MVNO takes over from the host mobile network operator (MNO). This spans from a “light” overlay, where the MVNO serves as a sales and marketing channel for the MNO’s service offer, to a “heavy” MVNO, where the MNO is only providing radio access network (RAN) for network coverage.
Cape is a heavy MVNO that operates its own secure, cloud-based, US-owned mobile core. By operating as a heavy MVNO, we have unique control over:
- SIMs, which serve as the root of trust for mobile networks. They authenticate you and hold keys.
- The Core, which controls who can connect to your phone, how data is routed, and whether legacy tech like 3G is allowed.
By owning both, we can:
- Securely authenticate users
- Block suspicious signaling messages
- Block insecure protocol fallback
- Enforce privacy policies at the network level
All your traffic—even while roaming internationally—routes back through this core. That means all your mobile traffic remains private from foreign telcos.
Secure Signaling Protection
Phones on Cape’s network don’t connect to outdated, insecure networks like 2G or 3G at all. This eliminates whole classes of SS7 and bid-down attacks. In addition, our Network Lock:
- Monitors for signaling attacks
- Detects when rogue networks try to connect to your device
- Alerts you when there are suspicious attach requests, and blocks connections from regions or networks known to be hostile
Connection without Compromise, Around the World
Most carriers treat roaming as a checkbox. Cape treats it as a threat surface.
Whether you’re a journalist in a conflict zone, a business traveler at a foreign summit, or just a traveler who values privacy, Cape gives you secure and private global coverage.
How to get started
On January 27th, 2026, Cape exited our beta and launched several new features, including Secondary Numbers, Secure Global Roaming, and Identifier Rotation (for iPhone & Pixel).