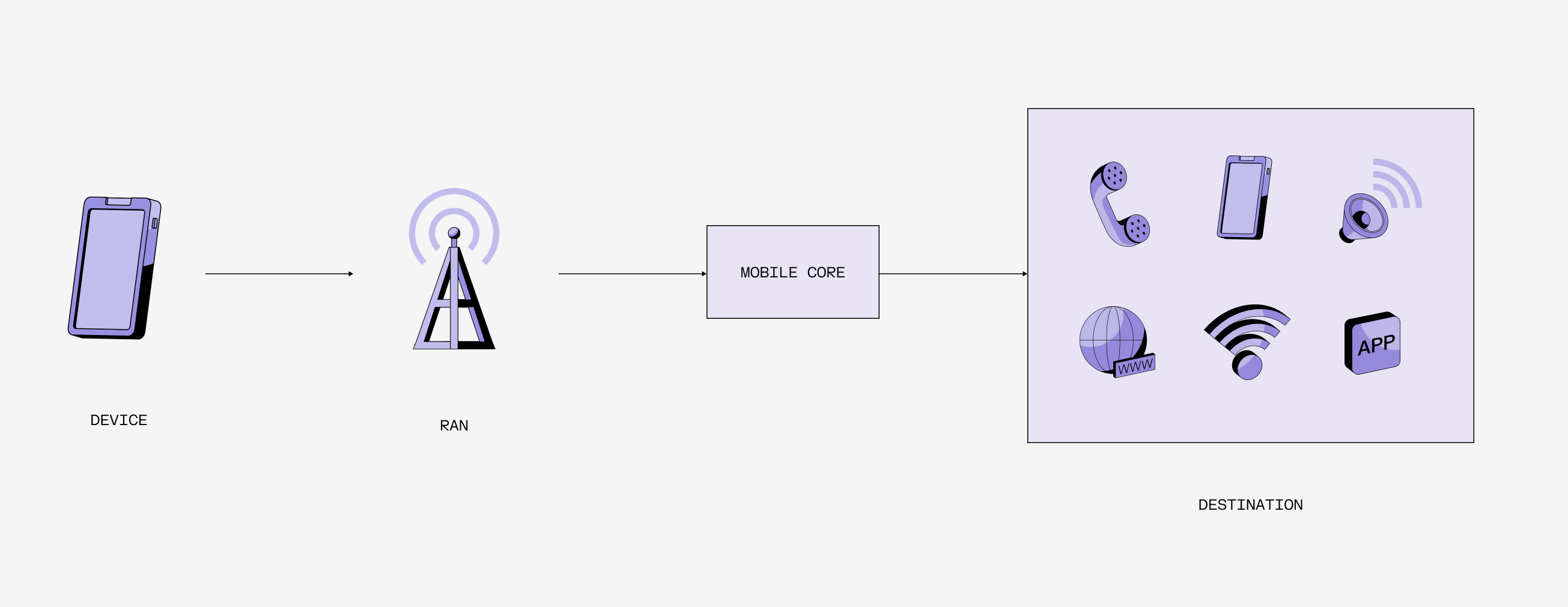
Cellular connectivity feels fast—instant, even. If you’ve ever called someone sitting right next to you, the speed at which their phone rings can feel like magic.
But that seamless experience masks a complex, global system operating behind the scenes.
In reality, your call is routed from your phone to the nearest cell tower, into your carrier’s network provider (known as the "core"), then to your recipient’s core, if your recipient is on another network. From there, it’s sent back out through a tower near them, and finally, their phone rings.
All of this happens in milliseconds—but the invisible handoff between towers and core networks is where telecom security lives or dies.
What Happens When You Make a Call
Here’s the simplified journey your mobile connection takes:
Device
Your phone, equipped with a SIM card, initiates the connection and requests access to the network.
RAN (Radio Access Network)
Think of this as a nearby cell phone tower. The RAN is your phone’s first stop on its way into the network. It includes:
- Spectrum: The radio frequencies your phone uses to transmit and receive data. These frequencies are leased by the government to telecom providers.
- Cell Towers and Antennas: The physical structures that transmit signals over those frequencies.
- Radio Equipment: The gear at the tower site that converts your phone’s signal into data that the network can understand.
In the United States, telecom providers that lease spectrum are required to also build and maintain this infrastructure. Almost all of the major carriers also have roaming agreements, which means they can utilize RAN that they don’t own and operate themselves. So for example, an AT&T subscriber could use T-Mobile RAN if the two companies have a roaming agreement.
Core Network
After your signal enters the system through the RAN, it gets routed to the core network—the brains of the operation. As noted above, the RAN and core network can be run by different entities.
The core is responsible for:
- Authentication – Making sure you’re a valid subscriber with the right permissions
- Routing – Sending your call, text, or data to the correct destination
- Policy Enforcement – Applying security rules, managing access, and controlling features like call blocking, network prioritization, or disabling legacy tech like 2G
This is where modern mobile security should live—but in most networks, it’s still built on legacy infrastructure vulnerable to attacks.
The Destination
Once your data or call has been authenticated and routed through your core network, it travels to its final destination. This could be:
- Another mobile device (if you're placing a call or sending a text)
- A server on the internet (like when you load a website or use an app)
- A content delivery network (streaming video or audio)
- A messaging platform or encrypted chat app
- Or anything else your phone is trying to reach
If the recipient is on a different carrier, your data may pass through their core and their RAN before reaching their device. If you’re accessing an online service, it exits the mobile network and enters the broader internet.
Cape secures your traffic all the way through our infrastructure—so even when the destination lies outside of our network, your side of the connection is locked down by default.
Who Owns Each Layer
Now that we’ve broken down the stack, let’s look at how different telecom companies interact with it.
Mobile Network Operators (MNOs)
Carriers like AT&T, Verizon, and T-Mobile are MNOs. They own and operate the entire mobile stack:
- They lease spectrum
- They build and manage towers (RAN)
- They run the core network
- They issue and manage SIM cards
MNOs control everything from the ground up—but their systems are often outdated, and difficult to modernize. MNOs also typically collect massive amounts of user data and frequently lose sensitive data in major breaches due to poor security practices.
Light Mobile Virtual Network Operators (MVNOs)
Carriers like Mint Mobile, Google Fi, and Cricket are Light MVNOs. They don’t own infrastructure. Instead, they:
- Lease access to an MNO’s towers, core, and spectrum
- Use the MNO’s SIM cards and security controls
- Focus on customer-facing elements like marketing, billing, and customer service
Because they don’t control the technical backend, light MVNOs inherit all the same security limitations and tracking liabilities of their host MNO, often reselling service under a different brand.
What about Cape?
We are a “heavy” MVNO, meaning we lease physical radio access from MNOs, but we retain control over two of the most critical software components of mobile service: the Core Network and the SIM.
And unlike traditional MNOs, our core is fully cloud based, and stripped of vulnerable legacy infrastructure. This allows us to implement privacy and security features that other carriers can’t.
Cape is the only privacy-focused carrier in the United States that runs all traffic through its own, fully cloud-based mobile core
The Core Network: The Brain of the Mobile System
The core is the central command center of a mobile network. When your phone connects to a cell tower, it’s really the core network behind the scenes deciding what happens next. By operating our own cloud-based, US-owned core, Cape has full control over:
- Authentication: This is the first step in confirming that a user is who they say they are and is authorized to use the network. It ensures your calls, texts, and data only reach you—and not an attacker.
- Policy Management: Cape can enforce precise rules about what devices can do on the network and how they interact with others. This allows us to deploy added privacy and security measures at the infrastructure level—not just in apps or device settings.
- Supported Technology: We can disable legacy tech like 2G or 3G, which are vulnerable to interception and SS7-based attacks.
- Signaling Protection: Signaling protocols, which are used to set up and route calls and SMS, can be abused by hackers. We monitor signaling activity across networks. If your phone receives connection requests from suspicious networks, Cape can detect and block these threats in real time.
- Call Logs: Most carriers generate detailed Call Data Records (CDRs), including who you called, when, for how long, and your location at the time of the call. Cape, on the other hand, has full control over what gets logged, how long it’s retained, who can access it, and how it’s encrypted. We retain only what’s necessary to provide reliable service, and nothing more.
- Secure Roaming: Call, message, and data traffic are routed from a foreign carrier to Cape’s core, which means that foreign carriers that are compromised or subject to local government law enforcement access cannot eavesdrop on your communications.
In short: Cape doesn’t just relay your traffic—we actively secure it.
SIMs: The Identity Key
A SIM card isn’t just what gives you a phone number—it’s a cryptographic identity that your device uses to authenticate to the network. MNOs treat SIMs as an application platform on your phone, which they often use to collect detailed analytics about you. Most MVNOs use SIMs provisioned by the host MNO, which limits their ability to secure or manage them. Cape, by contrast, issues and controls our own SIMs. That gives us powerful privacy capabilities:
- Authentication: SIMs securely transmit a set of credentials to the core network. If those credentials check out, your device is allowed to send and receive traffic. By controlling SIM issuance, Cape can ensure that these credentials are protected and never exposed to third parties.
- Profile Management: Your unique identity on the network—your IMSI (International Mobile Subscriber Identity)—is stored on the SIM. Cape manages these profiles directly, securing them against misuse.
- Identifier Management: Persistent identifiers like IMSIs are what adversaries use to track individuals across time and space. Because we control the SIM, Cape can manage these identifiers and how they’re logged, making it harder for anyone to follow your movements or target your device.
No other carrier provides this set of capabilities.
Cape’s infrastructure is purpose-built from the ground up with privacy and security in mind. And wherever you are in the world, all of your mobile traffic—calls, texts, data—routes through Cape’s secure, cloud-based core, protecting it from interception or manipulation by foreign carriers or surveillance networks.
Real Privacy Requires Ownership
Owning and operating our own SIM provisioning and mobile core gives Cape unprecedented control over your mobile privacy. We're not bogged down by insecure, legacy telco infrastructure. We’re running the network ourselves.
This isn’t the easy way to build a telco. But it’s the only way to build one that truly protects its customers.