If you called your oncologist a few years ago, there’s likely a log of it, including how long the call lasted and where you were at the time. If you texted an old friend afterwards, there’s a log of that too.
Call and text logs document every call and text you make or receive, including their duration and your location at the time.
Call logs reveal a lot about you…
Anyone with access to your call logs would be able to identify your closest relationships, locate your home and workplace, and reconstruct your daily routine at a level of detail and specificity that you yourself couldn’t achieve. Call logs remember what you’ve long forgotten, and are the most under appreciated pipeline of digital exhaust that you have.
…call logs persist for an unknown length of time…
Your mobile carrier probably does not tell you how long they keep your call logs. Most privacy policies state that they’ll retain your data for “as long as necessary to fulfill the purposes of this privacy policy”—a carte blanche. Only in 2022, in response to a request by the FCC Chair, did carriers reveal that they were keeping geolocation data for as long as five years–far longer than necessary to provide you with phone service. (So why do they keep it so long? To monetize it.) Prior to that, privacy advocate Malte Spitz famously sued his telecom in 2011 to obtain 35,000 detailed logs they had been holding about him. Malte reconstructed the logs into a surprisingly specific replay of his activities over the past several years.
…and call logs are easily obtained by hackers.
This data is frequently breached. For example, in 2024, hackers got the AT&T call logs of 109 million people, one in three Americans. The Salt Typhoon hack by China compromised every major US telco, meaning that even now China could potentially have access to the call metadata of any and every American.
Cape is built to forget.
We run our own mobile core. That means that unlike other mobile virtual network operators, or MVNOs, we produce our own logs. Other operators that control the physical cellular towers also generate logs, but we change traditionally static identifiers that the tower operators receive, which makes their logs less useful for tracking you by weakening their correlation to a specific identity.
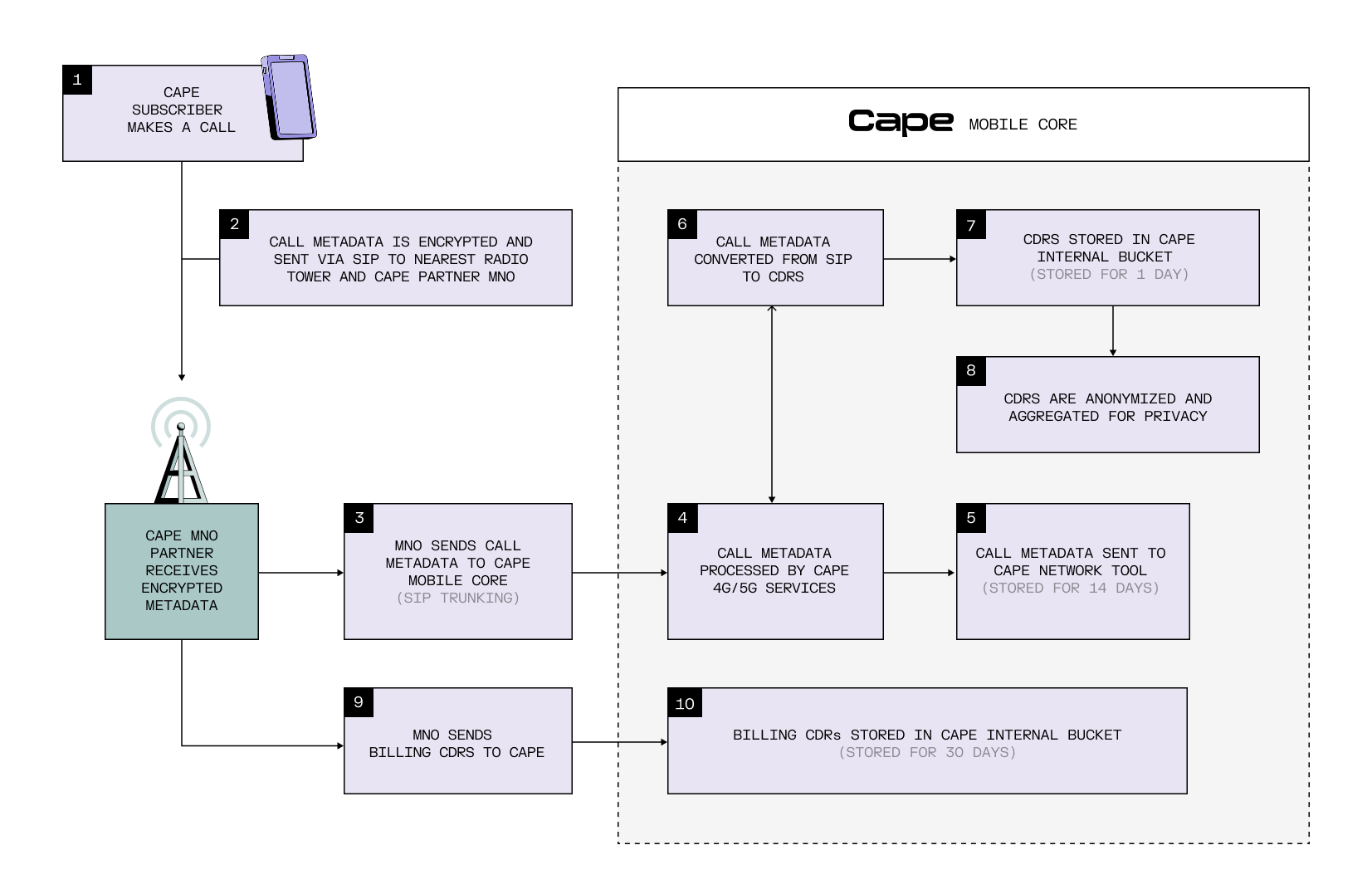
Here's how it works:
- A Cape subscriber makes a phone call.
- For supported devices, call metadata and text messages (caller number, recipient number, time of day, IMEI, text content) are encrypted by the phone using IPsec. The encrypted information is sent to the closest radio tower and then sent to a Mobile Network Operator (MNO) partnered with Cape. Partners are not able to decrypt call metadata.
- The MNO sends the encrypted call information to Cape's Mobile Core via a SIP trunking service.
- The call is processed by 4g/5g services inside Cape’s Mobile Core.
- Call information is sent to a Network Tool and is stored there for 14 days.
- Call information is converted from SIP into Call Data Records (CDRs).
- CDRs are stored in Cape’s internal CDR bucket for 1 day.
- Lastly, CDRs are anonymized by removing all personal information (IMSI, IMEI, phone number, location), and aggregated. This anonymized and aggregated data helps Cape measure usage of our network and detect issues while maintaining privacy.
- When Cape’s MNO partners bill Cape for using their mobile network, they send evidence of network usage in the form of CDRs (TAP3, NAPTRE, IOT). Some partners use a data clearinghouse to share this supporting evidence, while others send the CDRs directly to Cape.
- Billing CDRs are used by Cape to detect and dispute bills from partners, and are stored for 30 days.
Cape deletes call and text metadata in days instead of years.
While most carriers keep data for years, we keep your data for days.
The deep dive...
Inside Cape's mobile core, there are two sources for call and text logs: SIP messages and CDRs. SIP stands for Session Initiation Protocol, and it is used to manage calls and texts within Cape and between external networks like domestic roaming partners. Upon dialing a phone number, a SIP message is produced by the phone, encrypted for supported devices, sent to the Cape mobile core, and forwarded to the receiver's carrier. At the end of a phone call, there is another SIP message sent to end the session. SIP messages are stored by Cape for 14 days and are used for resolving network issues such as call drops and text failures. Call audio and text message content are never stored.
The other form of call and text logs are called Call Data Records (CDRs). Other carriers store CDRs for years and use them to track and profile you for advertising; Cape will never do this. CDRs are also used by carriers for business-to-business billing, which means a mobile carrier receives a bill from their partner alongside billing CDRs, and then compares it with internally generated CDRs. Think of it like a digital receipt for mobile service; both parties take note of charges that incurred, and then they compare and see if these charges line up.
Cape uses aggregated data for billing disputes rather than internally generated CDRs because we don't want to share your data with partner MNOs. We think it’s a worthwhile tradeoff to cut down on the huge amount of digital exhaust we produce as the price of connectivity, and helps us stay true to our promise of collecting and retaining as little subscriber data as possible.
Internally generated CDRs are deleted after 1 day and we only use them to create anonymized aggregated statistics of the network. CDRs that are shared by partners are stored for 30 days, which gives us time to process them and begin a billing dispute; specific activity that we believe to be fraudulent will not be deleted until the dispute is complete.