Premium, nationwide cell service for $99/month, with no hidden costs. Try your first month for just $30.


Your carrier tracks you. We don’t.
Most carriers start tracking you the moment you sign up.
They require your full name, home address, Social Security number, and email—before service even starts.
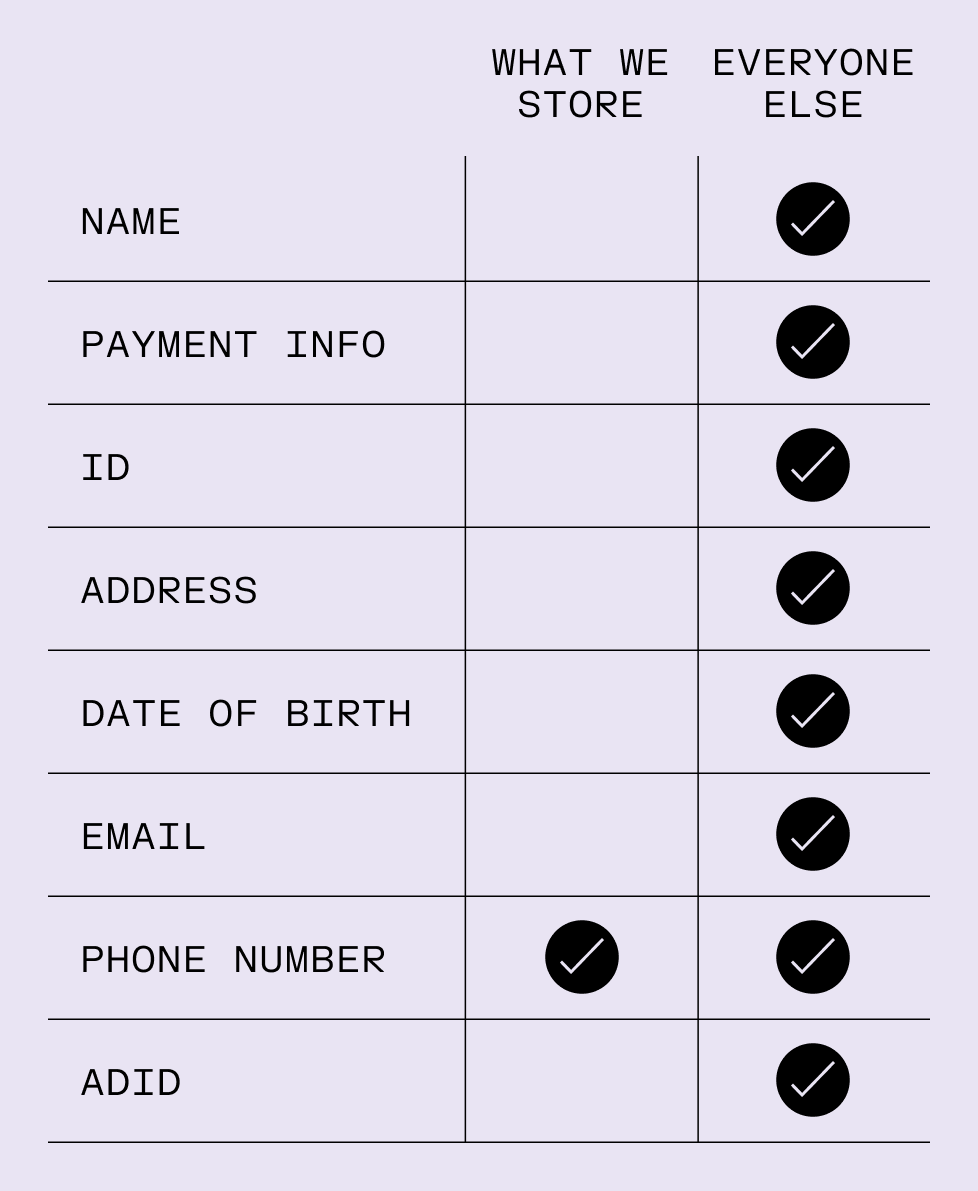
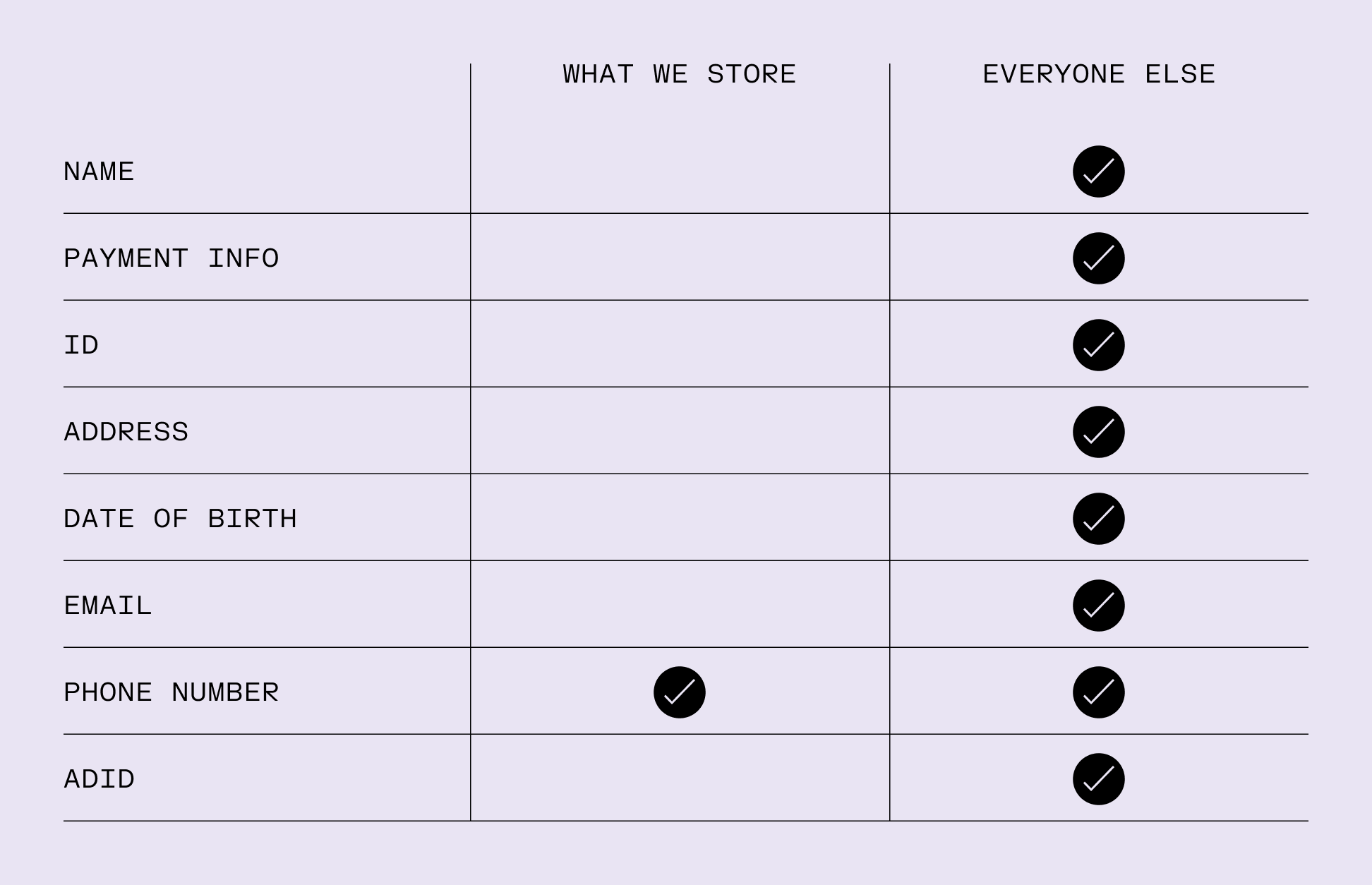
Personal information
collected by other carriers
Once you're connected, nearly everything is tracked.
Who you contact, where you go, which apps you use, and when. This information is logged, analyzed, and stored for years.
Then, it's packaged and sold.
Your data is shared with third-party vendors, ad networks, and data brokers who use it to build detailed profiles of your interests, movements, and relationships.
ADDRESS: 100 CAPE ST.
MARITAL STATUS: MARRIED
AGE: 35-49
INCOME: +$150K/YR
JOB: ENGINEER
Ad targeting
Advertisers buy data that tells them exactly who you are, where you've been, and what you care about. Personalized ads are powered by intimate surveillance.
Credit/loan approvals
Financial institutions use third-party data to assess your creditworthiness. What you buy, where you travel, and how often you move may influence your access to credit.
Background checks
Employers and landlords increasingly rely on data vendors that aggregate your online footprint—often without context or consent.
Landlord rental decisions
Location histories, spending habits, and even social media behavior can be used to determine whether you get approved for a lease.
When they’re not selling your data, they’re losing it.
Outdated systems and weak security allow hackers to breach customer data–often compromising millions.

In April 2025, security researcher Evan Connelly identified a significant vulnerability within Verizon's Call Filter iOS application. This flaw allowed unauthorized access to the incoming call logs of Verizon Wireless customers. Specifically, the application's network request to retrieve call histories did not properly validate that the phone number being requested matched the authenticated user's number. As a result, an attacker could modify the request to access call data for any Verizon number, not just their own.
The exposed data encompassed detailed incoming call records, including phone numbers and timestamps. This breach posed substantial privacy and security risks, particularly for individuals in sensitive positions such as journalists, law enforcement officers, and public figures. The ability to access and analyze call metadata could enable malicious actors to reconstruct personal relationships, monitor communication patterns, and potentially compromise the safety of targeted individuals.
Verizon was alerted to this vulnerability and took measures to address the issue promptly. However, the incident underscored the critical need for stringent security protocols in applications handling sensitive user data, as well as the potential dangers posed by seemingly minor flaws in software design.

On October 12th, 404 Media reported a breach of Verizon’s push-to-talk (PTT) systems, which are a separate product marketed toward public sector agencies, enterprises, and small businesses to communicate internally. The hackers, Cyberphantom and Judische, posted the stolen data for sale to a Russian-language cybercrime forum, saying that the author was “selling American telcom access (100B+ Revenue)... access includes several admin accounts with admin level rights, apis, interconnected LAN servers, and more. Data includes call logs, emails, phone numbers, addresses, names, and more. Current data amounts to over 900 GB. Price: 200K USD minimum, negotiations are open, serious buyers only.” Public procurement logs show that potential Verizon PTT customers include local and state governments including sheriff deputies, as well as government agencies like NASA and the Army.

In October 2024, the Wall Street Journal reported a significant breach by Chinese hackers, identified as "Salt Typhoon," targeting at least eight major U.S. telecommunications providers, including AT&T, Verizon, and T-Mobile. This cyber-espionage operation aimed to identify individuals or groups within China who were being monitored by American intelligence agencies. The hackers infiltrated lawful intercept systems and accessed broader internet traffic, maintaining unauthorized access for months. Subsequent investigations revealed that Salt Typhoon's activities were more extensive than initially understood. They accessed sensitive metadata of a large number of Americans, including call logs and, in some instances, unencrypted text messages and call audio. High-profile individuals, such as President-elect Donald Trump and Vice President-elect JD Vance, were among those targeted. In response, U.S. senators have called for enhanced security measures to protect national infrastructure. Senator Ben Ray Luján described the incident as possibly the largest telecommunication hack in American history, emphasizing the need for preventative actions. The FBI and the CISA have urged telecom companies to bolster network security to prevent future incidents.

On Friday, July 12th, AT&T suffered a massive cyberattack as data from around 109 million customer accounts (nearly all of AT&T’s customers), containing records of calls and texts, was illegally downloaded to a third-party cloud platform. The compromised files contain call and text records of AT&T cellular and wireless customers, as well as AT&T landline customers interacting with those cell numbers, between May 2022 and October 2022. The stolen data also includes a small number of customer records from January 2, 2023. The files do not contain the content of the calls or texts, or any personal information such as SSN, but some of the records include cell site identification numbers that can be used to determine the approximate location of where a call was made or text was sent. AT&T said they first learned about the data breach in April 2024, but delayed public notification based on determination by the Justice Department. The FBI is still investigating the breach origins, but at least one person has been arrested so far.

On March 30th, 2024, AT&T disclosed a data breach affecting 7.6 million current and roughly 65.4 million former customers, with sensitive data leaked on the Dark Web. The first indication that a security incident may have occurred was in August 2021, when a hacker posted a data sample and offered the sale of a massive data set they claimed to have stolen from AT&T. At the time, AT&T denied that a breach of their systems had occurred, stating that the data likely originated from another source. In early March 2024, a data seller allegedly published the full data set, revealing information from 73 million AT&T account holders. Following confirmation of the breach, AT&T notified affected individuals that their personal and account information—including names, email addresses, postal addresses, phone numbers, Social Security numbers, birth dates, and account details—might have been compromised. This incident left customers vulnerable to identity theft and financial scams, and led to demands for improvements in AT&T's data security protocols. See this article to learn more about steps you can take to protect your privacy and avoid falling victim to future data attacks.

On February 7th, 2024, a report was filed to the Maine Attorney General on behalf of Verizon announcing that their company suffered an internal data breach. While the breach occurred on September 21st, 2023, the company didn't discover what had taken place until nearly three months later on December 12th, 2023. An investigation uncovered that a Verizon employee had gained unauthorized access to a file containing sensitive information of over 63,000 employees, including names, Social Security numbers, physical addresses, and more. Affected employees were offered access to identity protection and credit monitoring services in order to prepare for possible identity theft, fraud, and stolen funds.

Toward the end of 2023, Mint Mobile notified an unknown number of customers via email that they had suffered a security breach. The email stated that “an unauthorized actor obtained some limited types of customer information." While the company stated that the underlying issue had been resolved, and that information like Social Security numbers and credit card information was not at risk, the data obtained did include things like customer names, phone numbers, email addresses, and SIM and IMEI numbers, placing those customers at risk for SIM swapping and other social engineering scams. Mint Mobile has since been acquired by T-Mobile.

On September 20th, 2023, T-Mobile customers took to social media to report that upon logging into their T-Mobile apps, their accounts displayed the personal information of another customer instead of their own. Consequently, sensitive data, including addresses and credit card information, was exposed. T-Mobile responded to the breach, reporting that it was caused by an overnight system error and affected fewer than 100 customers. However, the full extent of the exposure remains unknown, as the number of parties has not been disclosed. This incident marked the third customer-related security breach for T-Mobile, and the fourth involving a breach of T-Mobile information, in 2023 alone—an unprecedented record of privacy and security violations for a telecom company in a single year.

Reports emerged on September 21st, 2023, revealing that hackers breached T-Mobile's internal servers in March 2023, extracting a massive amount of highly sensitive employee data. The compromised information, totaling 89 GB, encompassed details of 17,835 past and present employees, such as names, partial Social Security numbers, and email addresses. This data was subsequently posted on a well-known hacker forum. It is speculated that the breach originated from Connectivity Source, an independently owned T-Mobile dealer, in April 2023.

In April 2023, T-Mobile sent a letter to 836 customers disclosing that a data breach had occurred earlier in the year. Information obtained for each customer varied but may have included full name, contact information, account number and associated phone numbers, T-Mobile account PIN, Social Security number, government ID, date of birth, and more. While this breach affected a much smaller number of customers than the incident reported in January, which affected over 37 million, it still represented a massive failure of T-Mobile's security measures. For over a month, cyber attackers were able to maintain ongoing data theft operations while remaining undetected. During that time, affected customers were at enhanced risk of experiencing fraud or phishing scams without any warning to be on guard.

In January 2023, the data of 7.5 million Verizon wireless customers was found on the Dark Web. The breach, discovered by the cybersecurity team SafetyDetectives, was linked to Verizon by clues discovered hidden in the filenames, but conclusive origins have never been disclosed. In response, Verizon stated that the issue stemmed from an outside vendor and had been resolved. While the exposed information did not include any personally identifiable data, the researchers believed that it could be combined with information from other breaches, giving attackers a higher chance of success in perpetrating fraud or identity theft.

In January 2023, T-Mobile discovered that a "bad actor" had stolen information from over 37 million customer accounts via unauthorized use of a single API. Personally Identifiable Information (PII) including names, addresses, phone numbers, and dates of birth was exposed during the breach. This incident highlights the danger of uncontrolled and unmonitored API use that often occurs at massive companies like T-Mobile. Moreover, while T-Mobile reported that they were able to contain the attack in less than one day, a third of their total subscribers had their personal information exposed during that period.

Verizon experienced a data breach in October 2022 in which the last four digits of some customers' payment card numbers were exposed. While exposure of the last four digits alone would not enable unauthorized purchases, it did provide the attackers with personal details such as names, phone numbers, and addresses that could facilitate access to additional account information. Further, there's a possibility that the attackers were able to conduct SIM swaps on some accounts. A SIM swap could allow interception of messages or calls intended for the account holder via another device, potentially compromising other accounts. Verizon took steps to safeguard the impacted accounts, such as resetting personal identification numbers. The company also provided recommendations to customers on protecting non-Verizon accounts that may be at risk of unauthorized access through SIM swapping activity resulting from this incident.

In August 2022, a cybersecurity firm reported intercepting a sizable dataset containing Personally Identifiable Information (PII) on approximately 23 million individuals in the United States. The PII included names, physical addresses, email addresses, phone numbers, Social Security numbers, and dates of birth. According to the firm's analysis, the data corresponds most closely to past and present customers of AT&T. While AT&T did not outright confirm the data originated from their systems, they noted the records do not appear to match any known breaches of their own networks. It remains possible the incident is related to a prior data compromise at another unrelated organization.

In May 2022, an unauthorized individual allegedly obtained internal Verizon employee contact records through pretexting tactics. The individual reportedly used deception to access internal systems containing names, ID numbers, phone contacts, and emails. To monetize the stolen database, the alleged perpetrator requested $250,000 to safeguard the information and not publicly share it. Verizon stated they declined to engage, noting the information was already public. However, the database could allow bad actors to pose as employees or flood Verizon's email system with spam or malicious emails.

In August 2021, T-Mobile suffered one of the most extensive and costly data breaches on record. Hackers infiltrated T-Mobile systems and stole highly sensitive customer information, including names, driver's license numbers, Social Security numbers, and device identification numbers. In June 2022, T-Mobile reached a settlement agreement to resolve a class action lawsuit filed by customers affected by the breach. As part of the settlement terms, T-Mobile agreed to pay $350 million to customers who experienced harm as a result of the incident. Additionally, T-Mobile committed $150 million toward enhancing its cybersecurity protections and systems. The wireless carrier acknowledged the need to further strengthen safeguards for customers' private data.
Cape was built from the ground up with privacy and security at its core.
Our principles are simple:
We collect the minimum amount of data needed to provide our service.
Any data we do collect is stored for the minimum amount of time possible.
We never sell your data. Period.

Switch to Cape, America’s privacy-first mobile carrier.
Premium, nationwide cell service for $99/month with no hidden costs.
Trusted by Privacy Experts

Dmitri Alperovitch
Co-Founder of Crowdstrike
Stay anonymous.
Minimal Data Collection
We only collect the minimum amount of data needed to provide you service.
Private Payment
Pay for your subscription without handing over your name or credit card details to Cape.
Stay untraceable.


Identifier Rotation
Protect yourself from persistent tracking by rotating your IMSI every 24 hours, so you appear as a new subscriber each day.
Secondary Numbers
Get 2 free additional last-mile encrypted lines to use publicly, while keeping your primary number reserved for family and friends.
Last-Mile Encrypted Texting
Protect your SMS messages with middle-to-end encryption delivered through the Cape app.
Encrypted Voicemail
Keep your voicemails truly private, so that only you can listen to them.
Stay protected.


SIM Swap Protection
Secure your number and prevent SIM swaps with a private key only you control.
Network Lock
Prevent attackers from tracking your location or intercepting your calls and texts via SS7 and signaling attacks.
Secure Global Roaming
Roam internationally in 50+ countries while routing traffic to our secure US-based core.
Premium, nationwide 4G and 5G coverage, with industry-leading privacy and security.
Security is only as good if it comes with you, and coverage only matters if you’re secure.

Switch to Cape in Just 2 Minutes
- 01
- 02
- 03
Activate Your eSIM
You're ready to go!
Switch to Cape in Just 2 Minutes
Be the first to know about feature updates, special offers, and privacy news.
$99/mo.
That’s the total price, with no hidden costs.
All taxes and fees included.
Cape has partnered with Proton, a leading provider of privacy-first technology, to offer our subscribers with Proton Mail, VPN, Password Manager, and more for just $1 for 6 months.
What You Get:
Cape has partnered with Proton, a leading provider of privacy-first technology, to offer our subscribers with Proton Mail, VPN, Password Manager, and more for just $1 for 6 months.
FAQs
What is Cape?
Does ID Rotation work on all devices?
How do I access Cape's new features?
Do I have to turn on Last-Mile Encrypted Texting? (iPhone users only)
How does the $30 trial work?
Can I use Cape as a second line?
Can I get the $30 trial and still use another promo code?
Does Cape offer family plans?
Do you support international roaming?
Does a Cape phone plan come with a phone?
Is my device compatible?
Can I transfer my existing phone number to Cape?
How is your network coverage?
What’s included in my plan?
How do private payments work?
Do you throttle or cap usage?
Does Cape provide real phone numbers?
More Questions?
See our full FAQ list here.
Don’t take our word for it.
I’ve switched over entirely
Dec 20 2025Cape is the best and first actually privacy-focused mobile carrier i've ever encountered. Dependable enough for mobile hotspot data when I need it, and I've seen as much as I've needed, to be convinced of their importance.
In The News
David Ignatius,
The Washington Post

Switch to Cape,
America's privacy-first mobile carrier.
Premium, nationwide cell service for $99/month with no hidden costs.