If you’ve ever received a push notification on your phone—about a new voicemail, a billing update, or even just a login alert—you probably didn’t think twice about who else saw it. But behind the scenes, every mobile push notification travels through infrastructure controlled by Apple or Google. And as reported by both Wired and 404 Media, those companies can—and do—share that information with third parties, including law enforcement agencies and foreign governments.
How do push notifications work?
Mobile apps generally rely on either Apple Push Notification Service (APNs) or Firebase Cloud Messaging (FCM) to deliver notifications. These platforms offer reliable, fast, and persistent delivery, which is why nearly every app uses them. But they also present a surveillance risk.
By default, Apple and Google can see the full contents of any push notification unless it’s encrypted. That includes:
- The message content
- The sender/recipient identifiers
- The app triggering the message
- Timestamps and device metadata
This data can be logged, retained, and handed over to third parties—sometimes without user consent or even knowledge.
Enter Cape
At Cape, we’re raising the bar for mobile security, and that includes the small but sensitive moments when your phone buzzes. Our Encrypted Notifications feature is the first system of its kind to fully encrypt mobile push notifications—from the content to the metadata—so that only your device can read them.
We’ve designed a system that retains the delivery guarantees of Apple and Google’s infrastructure—while eliminating their visibility into your messages.
Here’s how it works:
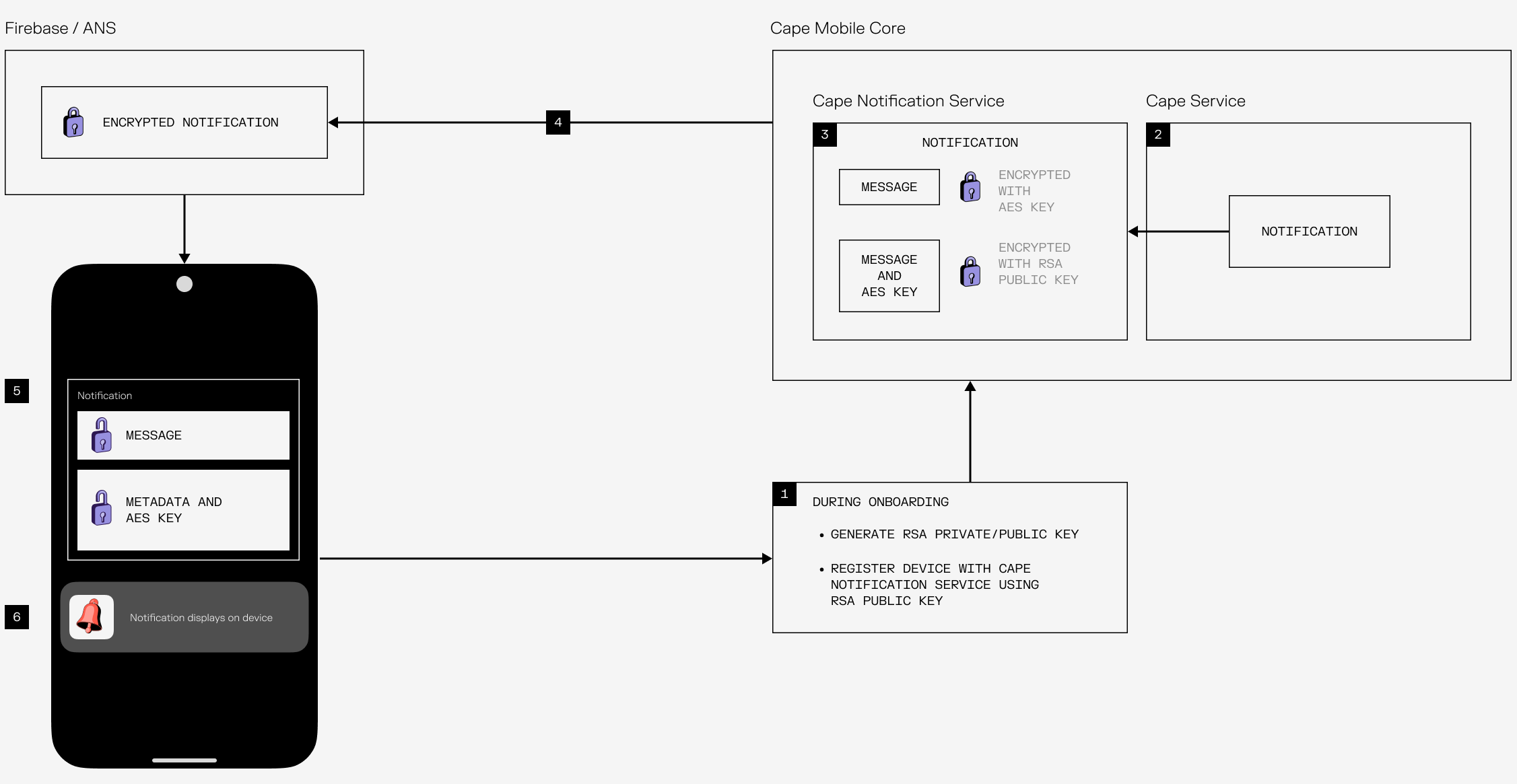
- During onboarding, your Cape device generates a public-private key pair dedicated to notifications, and your public key is registered with Cape’s secure notification service.
- Cape needs to send you a notification—whether it’s about billing, a completed number port, or an identifier rotation.
- The notification is sent to Cape’s notification service, where it is encrypted. The notification message is encrypted using a one time AES-256 key, and then the AES-256 key and other notification meta data is encrypted using your RSA public key. This ensures the notification can only be decrypted with the RSA private key stored locally on your device.
- The encrypted payload is then sent through APNs or FCM.
- The notification arrives at your device, where your private key decrypts the AES-256 key, and the AES-256 key decrypts the contents of the notification.
- Only then is the notification displayed on your device.
This ensures that once the notification is encrypted, no intermediary—including Apple, Google, or even Cape—can read your notifications.
Why this matters
Many of Cape’s notifications are sensitive by design. Alerts about SIM activity or changes to your account could indicate an ongoing attack or the need for immediate action. These moments demand strong security, not exposure.
Our encrypted notification system minimizes what third parties can see while reliably delivering your notifications. And it’s only a part of our larger mission to protect your identity. At Cape, we encrypt as much as possible, from data at rest to data in transit, to workflows like notifications to voicemail.
Privacy isn’t just about protecting what you send. It’s about how your device behaves at every level. Even when it buzzes.